- Create a new PGP key
- Copy the public key to GitHub
- Create a backup of the newly created key
- Test signing and maybe update .bashrc
- Signed Git commits and tags
- Publish the GPG key
- Restore the GPG key
Create a new PGP key
$ dnf install gpg
$ gpg --gen-key
# Enter your e-mail address and name:
Now, retrieve the public key id:
$ gpg --list-secret-keys --keyid-format LONG
/home/user/.gnupg/pubring.kbx
----------------------------
sec ed25519/485CAB7FC28F950B 2022-07-13 [SC] [verfällt: 2024-07-12]
47B43006BDDF5988443CDD7D485CAB7FC28F950B
uid [ ultimativ ] Firstname Lastname <user@domain.tld>
ssb cv25519/CED0142D1E47A615 2022-07-13 [E] [verfällt: 2024-07-12]
Note down the public key id (${GPG_PUBLIC_KEY_ID}). In the output above, 485CAB7FC28F950B is the public key.
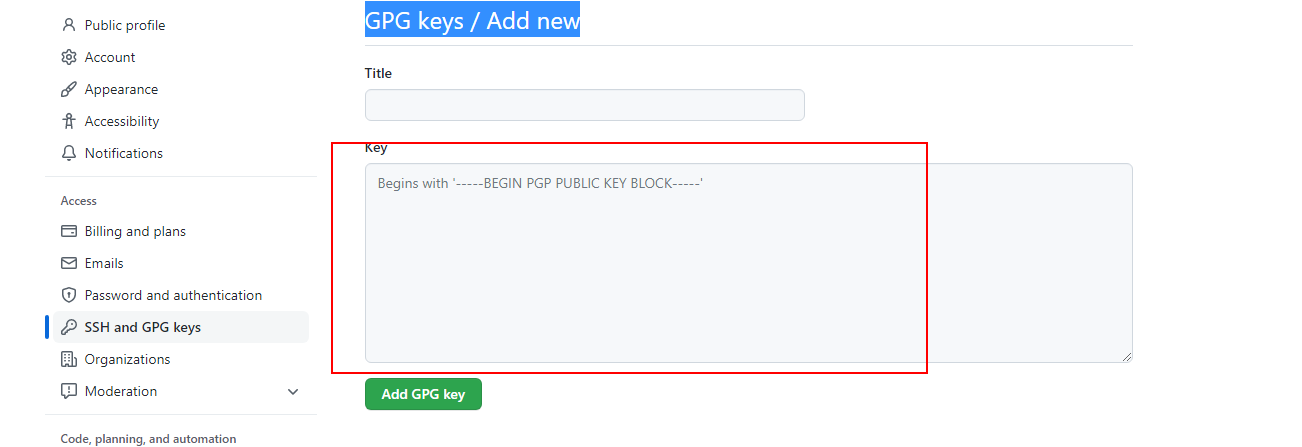
Copy the public key to GitHub
Retrieve the full public key:
$ gpg --armor --export ${GPG_PUBLIC_KEY_ID}
Go to GitHub's GPG keys section and paste in the exported public key:
Create a backup of the newly created key
$ gpg -o private.gpg --export-options backup --export-secret-keys user@domain.tld
Store the generated private.gpg in your password manager.
Test signing and maybe update .bashrc
Execute the signing command:
$ echo "test" | gpg --clearsign
If you receive the error
error: gpg: signing failed: Inappropriate ioctl for device
fatal: gpg: [stdin]: clear-sign failed: Inappropriate ioctl for device
you have to update your .bashrc to set the environment variable GPG_TTY:
GPG_TTY=$(tty)
export GPG_TTY
Do not forget to reload the .bashrc.
Signed Git commits and tags
# For your global configuration, set the signing key:
$ git config --global user.signingkey ${GPG_PUBLIC_KEY_ID}
Signing single commits and tags
If you want to sign commits and tags by yourself, you can use
# To sign a single commit:
$ git commit -S -a -m "A signed commit"
# To sign a tag:
$ git tag -s v1.0.0-signed
Signing all commits and tags
Instead of manually signing tags and commits, you can enable the signing by default:
# Enable signing of all commits:
$ git config --global commit.gpgsign true
# Enable signing of all tags, since GPG 2.23:
$ git config --global tag.gpgSign true
Publish the GPG key
$ gpg --keyserver pgp.mit.edu --send-keys ${GPG_PUBLIC_KEY_ID}
Restore the GPG key
In case of moving your GPG to another machine, you have to restore the GPG key. Retrieve the private key from your password manager and execute:
$ gpg --import-options restore --import private.gpg
# Edit imported key:
$ gpg --edit-key user@domain.tld
# Enter `trust`:
gpg> trust
# Enter `5` to trust the your key completely:
gpg> 5
# Confirm with `Y`:
gpg> Y
